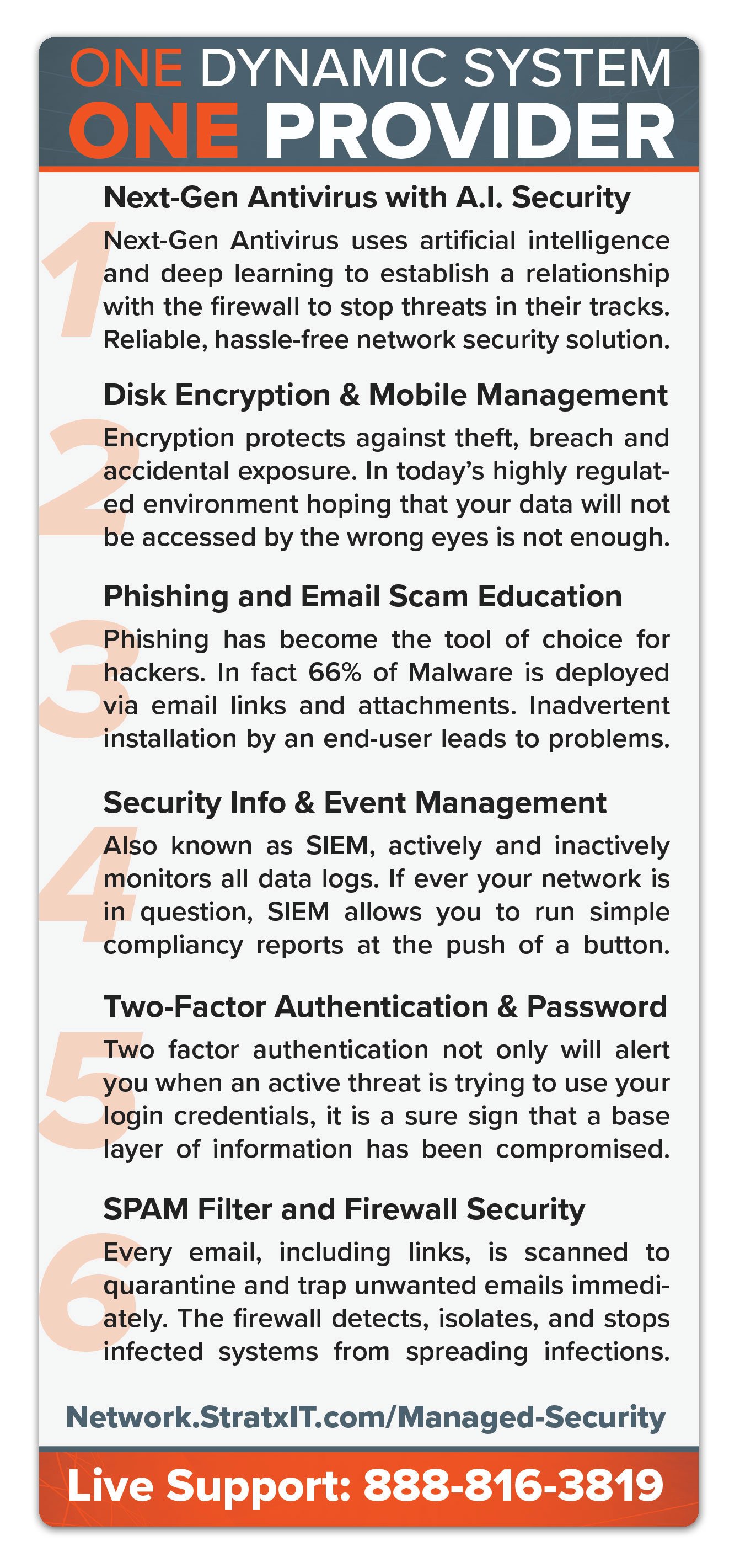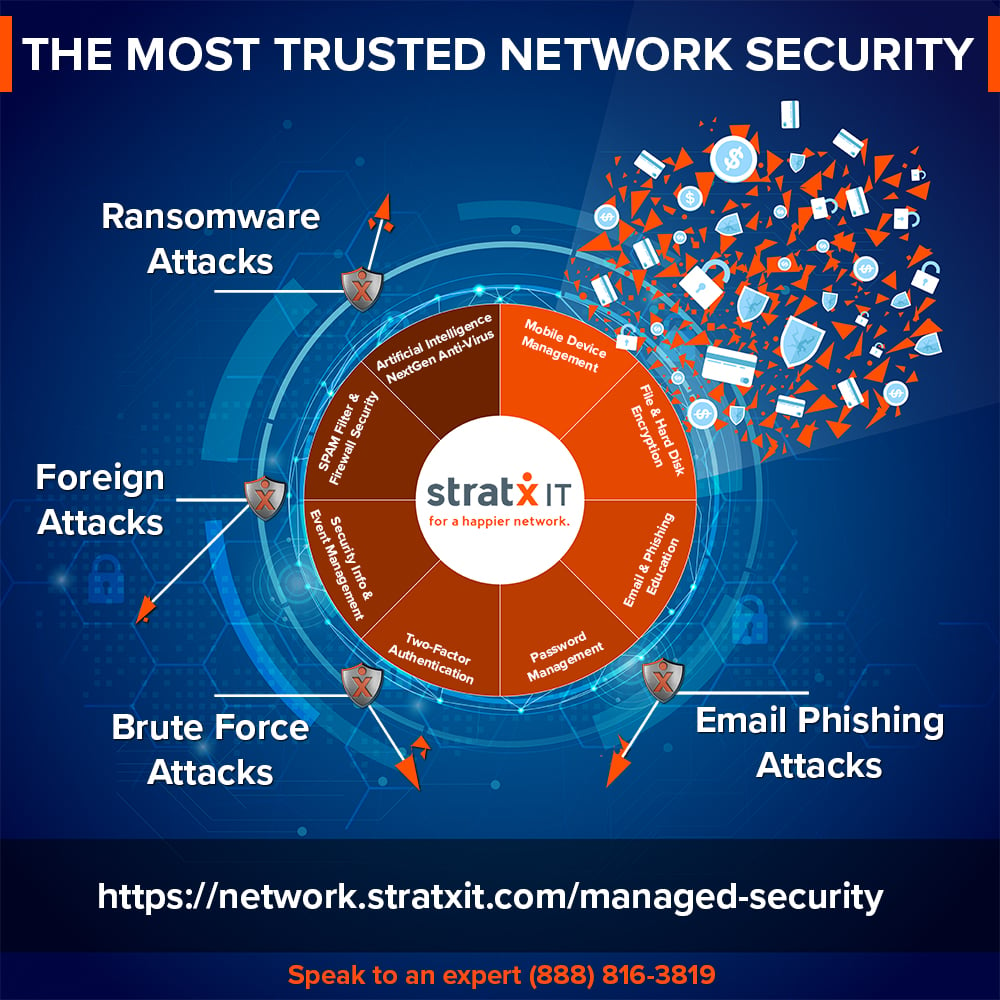
Data Security is more Relevant than Ever!
You may have recently heard of the Marriott? or Target? or Facebook? These are just a few of the headlined data breaches that alarmed our entire country. The reality is, these major data compromises are only what we hear about. It doesn’t reflect what actually takes place on a regular basis.
Internet hacking is real and it isn’t going away anytime soon. The truth behind many of these costly attacks is that many of these attacks were completely preventable. Hackers look for loop-holes and outdated softwares, such as Windows XP users. Many attacks begin with a simple phishing email, a hot link leading to a breach in the network. 2018, exposed many industry leading brands, such as:

These attacks are not only designed to affect large Fortune 500 companies either, John, a network manager in Dayton Ohio recently found this out when his 17-year old daughters Facebook account was hacked and duplicated to send malicious ransomware through. Talk about hitting close to home. This is why our team of industry leaders at StratX IT Solutions designed and launched the Integrated & Managed Network Security Bundle.
This bundle is perfect for Large Corporations as well as small businesses alike.
Securing your network and systems is a critical element of running your business. StratX IT offers a full suite of security components that in tandem, offer you the most up to date protection available managed by a single provider. A single provider means that you can rest assured that all systems are being cross-examined. Our proprietary system collects artificial intelligence metrics across your entire network, monitoring every email, loop-hole and entry-point 24/7. Other systems available only have access to bits and pieces which is an open-door to network vulnerabilities. How Secure is your Network? Take our Self-Assessment now to check for open vulnerabilities.