
Human error is one of the most common and least avoidable network security threat in any organization. Though some human related security risks arise from malicious intent, most do not. Honest mistakes don't come with intent but the damage is the same and can be incredibly costly. You need a robust and clearly communicated plan that is continually managed to limit your risk.
Taking Action to Secure Your Business Systems
It's essential to develop and adhere to best practices to reduce the human factor in security risks as it relates to employee education, the "IT guy's" ongoing due diligence, and management's mandate for security policies and practices. Policies are only as good as their enforcement. At least one study found that almost half of employees say their company has a security policy, but the staff do not follow it.
Employee: Education
Education: Human error is caused by lack of security policies, protocols and quite frankly, users just not knowing the risks. Train employees on your security requirements and expectations, why they're important and any penalties associated with not complying. Ongoing security education through weekly reminders is a great way to have employees keep security top of mind.
Learning to identify and avoid clicking on phishing emails is critical. Viruses like ransomware prey on uneducated users to the tune of millions of dollars in ransom and lost productivity.
On-going due diligence: Your IT guy's job is now network security and infrastructure
Security Risk Assessment: An on-going process of discovering, correcting and preventing security problems. This is an integral part of a risk management and determining security gaps within an organization. A properly conducted assessment will map out technology workings, workflows, interactions, systems and evaluate each element of connectivity, access and the technology needed to secure all of the interacting pieces.
Vulnerability Scans: You should run vulnerability scans on your systems on a regular basis -- at a minimum, annually. You should also run a scan after any network update or upgrade. Even the best planning is fluid in some areas and adjustments need to be made for security. Testing your systems allow you to "know what you don't know."
Management: Mandated security policy and practices
Employee Background Checks: Knowing who is on your staff is crucial to protecting your systems. Run comprehensive criminal and background checks as a condition of hiring.
Privacy and Internet Use Policies: Both your staff and clients should have an understanding of your privacy policy. This may help you avoid inadvertent breaches. Your staff should also read and sign an internet use policy, including limitations on what they can download to their computer.
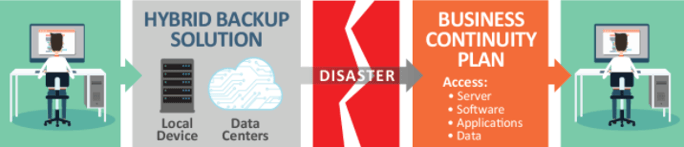
Business continuity and disaster planning: Even the best education and technology solutions are not 100% impenetrable. Dedicating time and funds to business continuity and disaster planning may be the difference that allows your business to recover in the face of a human or cyber disaster.
Backing up all data, programs and servers to a backup device onsite as well as on the cloud allows you to immediately mobilize within your office when a disaster strikes within hours vs. days.
Employees, IT and management in-sync
Cyber security is more than a matter of upgrading technology. Organizations must set the tone while looking at the complete security picture related to people, processes, and technology to manage the human factor of cyber security (malicious or other). Create awareness of potential errors caused by carelessness or lack of process, with employee education, detailed procedures, and the proper technology. This way, employees can play a part in safeguarding your business by identifying new possible risk and suspicious activity.


